Proofpoint email security architecture offers a variety of benefits. It delivers fast, secure access to information, and it defends against advanced threats. In addition, it provides separate data and encryption and gives intel about potential risks and threats within cloud apps. Proofpoint email security architecture offers excellent protection for your email and files. By using this technology, you can ensure that your information is secure and can be accessed quickly. In addition, you can take advantage of the product’s compatibility with Microsoft Office 365. You can also expect the security of your data to be protected against sophisticated attacks.
Table of Contents
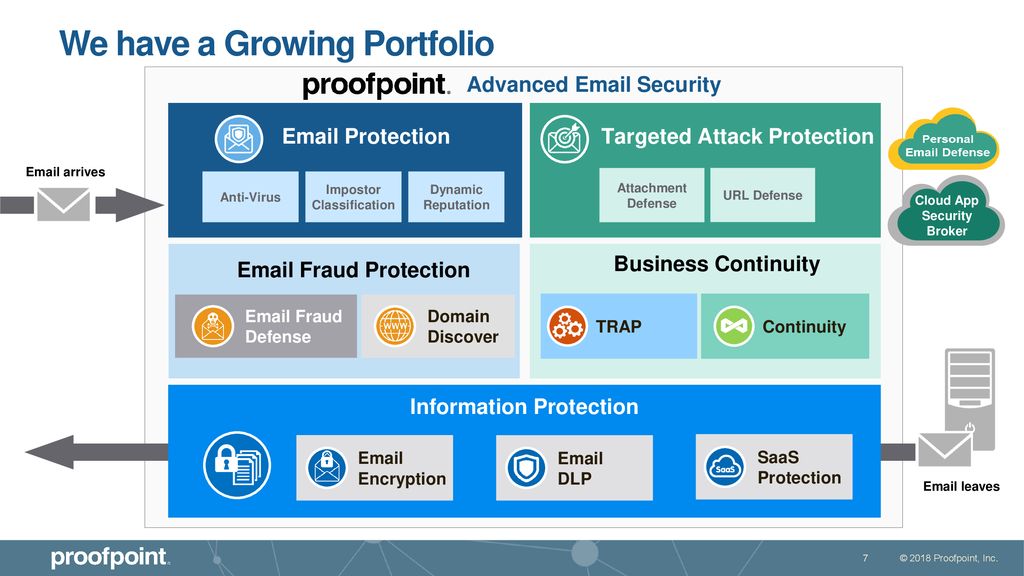
Protection From Sophisticated Attacks
Proofpoint is a leading cybersecurity company known for its advanced email security architecture. Its suite of cloud-based solutions is designed to help organizations protect their most important assets. Using machine learning and analytics, it can identify and eliminate targeted threats.
It is a complete solution that combines speed and innovation. Designed for businesses of all sizes, the company’s suite includes email protection, security monitoring, and data loss prevention. Powered by its advanced cloud architecture, Proofpoint can be easily deployed and adapted to meet any organization’s needs.
A new Proofpoint threat detection platform leverages machine learning and analytics to identify and prevent advanced threats. The platform is designed to provide actionable intelligence on Very Attacked People (VAPs) and helps security teams identify and prioritize remediation efforts.
In addition, Proofpoint’s email protection can catch unknown threats before they hit users’ inboxes. Users can block certain email types, or tag emails they suspect are suspicious. The system analyzes an email’s body, header, and message components to identify the content, the sender’s IP address, and more.
Fast, Secure Access To Information
Providing fast, secure access to information is essential for any organization. This is especially true with email archives, which must address many user requirements.
Email protection from Proofpoint provides organizations with the security and visibility they need to protect their most critical data. It also identifies threats and allows users to block unwanted emails easily.
Another key benefit is maintaining control over who gets to access and archive email. Users can define acceptable use rules and create block sender lists. They can even move emails to a lower priority or promote them to a higher one. The Proofpoint security architecture offers a unified user interface, which streamlines email security management.
In addition to blocking emails, Proofpoint can detect malicious attachments, URLs, and polymorphic malware. It also performs content analysis and reputation management.
Another key benefit is the ability to manage insider threats proactively. With a common content classification, a company can easily identify which documents are sensitive and can quickly notify their security teams of any sensitive information circulating across their networks.
Compatibility With Microsoft Office 365
Microsoft Office 365 is an Internet/Cloud-based subscription service that includes premium Office applications. It also provides other productivity services, such as Outlook. The service is offered monthly, with 1 TB of cloud storage for documents. Depending on the type of PC, the version of Windows you have installed, and the Office program, you may need to upgrade to a more recent version to get full compatibility with the new Office interface.
There are several ways to install and update Microsoft Office 365. You can do so through the Microsoft website, or you can use the Click-to-Run method. This is designed to reduce download times for Office client products.
While it isn’t possible to ensure compatibility with Office 365 for all of the Office programs you have installed, you can do a quick check. Check the software version you have and then look to see whether it is 32-bit or 64-bit. If it is 64-bit, you can upgrade to a newer version.
Defends Against Advanced Threats
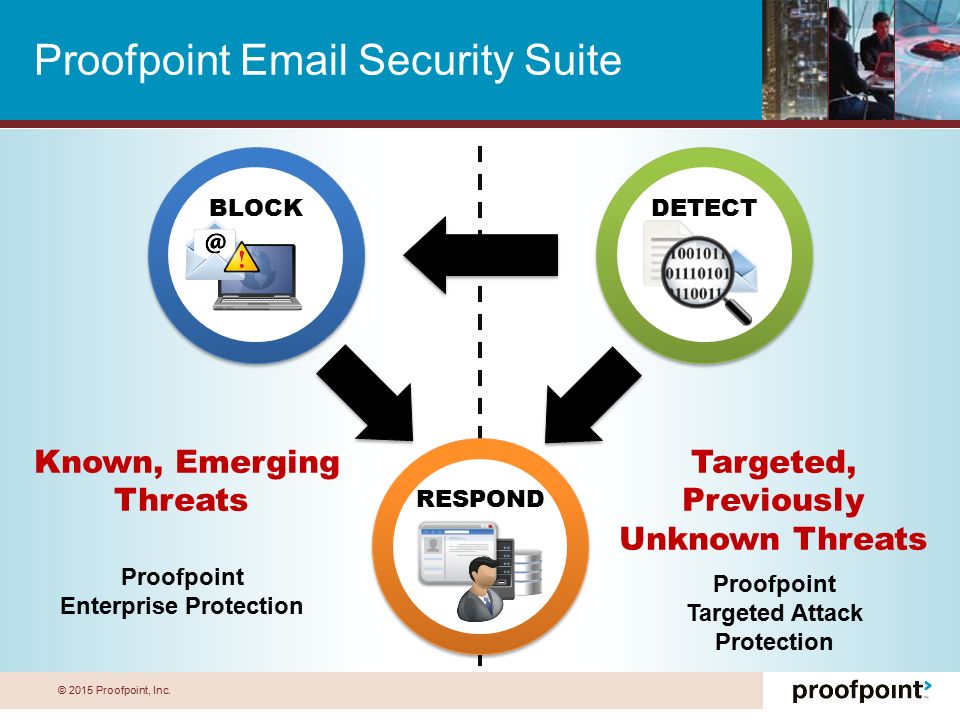
The Proofpoint security platform provides organizations with the protection they need against advanced threats. These threats often involve sophisticated email attachments that are crafted with malicious code. In the case of these threats, Proofpoint can stop and prevent them before they get to their targets.
The Proofpoint email protection service analyzes your emails for potential threats and helps you block them. It also allows you to tag suspicious messages and quarantine them. This function uses multi-layered threat protection, including machine learning. You can filter emails based on message headers, sender credibility, and message components.
Using machine learning, Proofpoint identifies and blocks malware and BEC attacks. It also protects against supply chain attacks.
Advanced Threat Protection offers businesses and consumers a comprehensive view of the email threat landscape. It includes data on more than 40 threat categories. It also offers insight into the most advanced threats. You can stop and respond to today’s most dangerous threats with this information.
In addition to its detection capabilities, Proofpoint provides users with behavioral insights. Through its PhishAlarm button, you can report suspicious messages directly to your security team.
Delivers Fast, Secure Access To Information
With Proofpoint’s email security architecture, your organization can rest assured that your critical information is always available and secure. By leveraging cloud-based technologies, Proofpoint helps protect your most significant risks while delivering productivity gains and cost savings.
The company’s email security architecture is built on the Cloud and has a host of advanced features that are designed to protect your enterprise from today’s most sophisticated attacks. It provides comprehensive threat reporting to help you keep tabs on your organization’s overall attack landscape. Your business will be prepared to respond faster to the latest threats.
Proofpoint is one of the leading providers of cyber-security solutions in the industry. This company uses patented DoubleBlind Encryption(TM) to encrypt your data before it leaves your organization’s firewall.
Proofpoint also has a robust suite of products designed to give you complete control over your business email network. You can set up a custom antivirus policy and firewall rules to ensure your emails are safe and secure. In addition, Proofpoint provides you with detailed reports and a knowledge base.
Delivers Separation Of Data From Encryption
The Proofpoint enterprise cloud architecture is a proven email archiving solution built for the modern era of email. It’s got the goods and the good stuff, which means fewer headaches for your IT staff. As your business grows, so does your need for an effective email archiving solution. And, if you want to reclaim the productivity and satisfaction of the modern era, you need a dependable email management plan that delivers a predictable and reliable email experience, which is no small feat in today’s fast-paced world.
What’s more, Proofpoint is the only cloud service that lets you keep control of the lion’s share of your communications, which is critical to achieving your productivity and retention goals. Using the cloud, your employees can access their mail through a secure, branded email experience that keeps the email inbox clutter-free and your employees productive, instead of just a black hole of information. Moreover, the Proofpoint enterprise has the best email security architecture, which means you get the peace of mind you deserve.
Delivers Intel About Potential Risks And Threats Within Cloud Apps
When you use cloud applications, there are risks and threats that you may not even be aware of. Luckily, there are tools to deliver intel about these risks and threats within cloud apps. These tools are called Threat Analytics Platforms (TAP). TAP uses machine learning to identify risks and threats in applications. It detects a variety of attacks, from credential theft to email-related attacks. The software can analyze the data and then apply machine learning to find patterns and trends. This intelligence allows TAP to adapt to attack techniques and learn from the results of attacks. Using a cloud application that has TAP installed can help your company mitigate the risk of malicious threats.
Another benefit of using a TAP is that it can provide insight into cross-vector threats. A biomedical research lab, for instance, may have to upload large amounts of data to the cloud. If they can’t transfer the data, they may encounter a bottleneck that prevents them from performing the required tasks.
